Learn the shocking details behind the recent attack.
Have user accounts been compromised too? Shall we worry about credit card details saved on the platform? Let’s find it all out.
Recently we all froze in anticipation at first due to the rumours of the taxi and food-delivery giant being hacked. This rumour then shortly followed by an official statement released by Uber.

How did it happen?
On September 16 it became first known from Twitter and Telegram posts shared by “vx-underground”, a project that collects and shares malware samples, that the technical giant has been compromised in many ways. According to vx-underground the threat actors “have completely compromised Uber. They have posted screenshots of their AWS instance, HackerOne administration panel, and more.”:
Initial tweets confirm Uber AWS, Slack and HackerOne panels being hacked. Moreover, Uber Financial data has been compromised and shared online. vSphere, Google workplace and more AWS data have been disclosed.
It’s known that the hacker have posted a general announce on Uber Slack. It has been stating that the company has suffered a data breach, however, the announcement has been perceived as a joke by the employees. Here’s a screenshot:
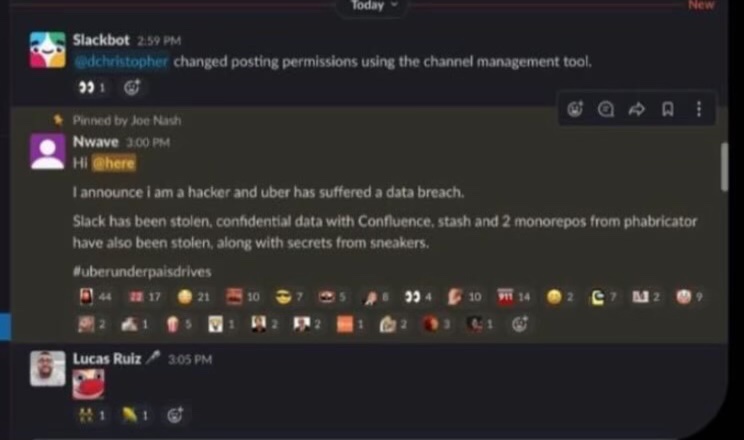
An ethical hacker Corben Leo has shared more details on how exactly the threat actors were able to compromise entire Uber infrastructure.
According to Corben, the hackers have accidentally obtained Thycotic admin user credentials stored in PowerShell scripts. They then managed to trick an employee to share sensitive information about Uber VPN. According to one of the versions, the hacker spammed the employees Duo for over an hour, then reached out to them via Whatsapp, saying they were from Uber IT. The employee have then approved the 2FA. Once they got VPN, it allowed the threat actors to scan entire Uber intranet, identify services used and their potential vulnerabilities.
Who has breached Uber?
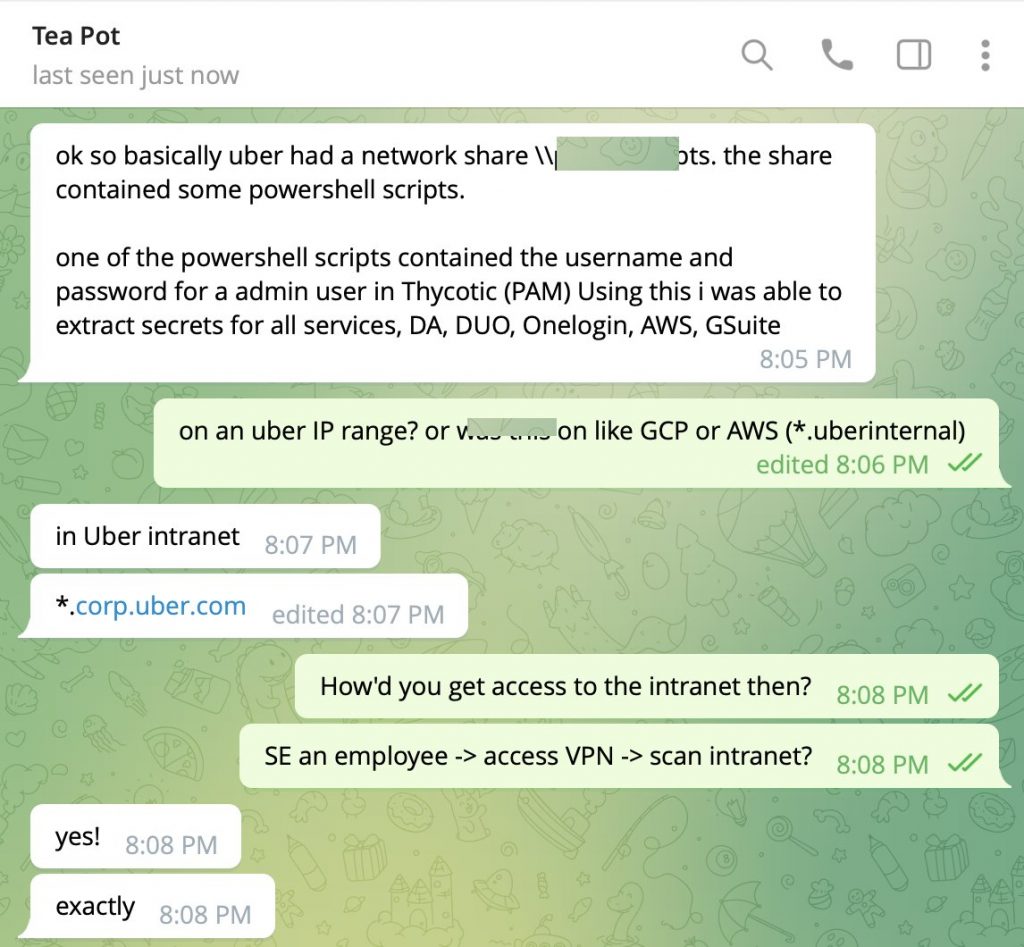
Corben has shared a conversation with a hacker clarifying vector of the attack. The Uber breach has been attributed to a threat actor under alias teapots2022.
Uber, in their turn, have accused LAPSU$ hacking group or its affiliates in the recent attack. The company sees similarities in techniques used by the group in compromising other companies, as Samsung, NVIDIA, CISCO, Microsoft, Okta and others in 2022 alone. Official press release can be found here.
What does it all mean for Uber users?
Uber states that:
First and foremost, we’ve not seen that the attacker accessed the production (i.e. public-facing) systems that power our apps; any user accounts; or the databases we use to store sensitive user information, like credit card numbers, user bank account info, or trip history. We also encrypt credit card information and personal health data, offering a further layer of protection.
Company has assured that no changes to codebase have been done. An internal financial tool managing part of invoices has been affected, but it does not concern the users. The investigation and response efforts are still ongoing.
Stay up to date with exposed information online. Kaduu with its cyber threat intelligence service offers an affordable insight into the darknet, social media and deep web.