Unmasking the New Cyber Threats and Celebrating Security Victories
The cyber security landscape is a dynamic and ever-evolving field, with new threat actors emerging and existing ones being apprehended. The first week of July has been no exception, with a flurry of activity that has kept the cyber security community on high alert. Here’s a recap of the week’s most significant events.

1. New Ransomware Players: “Underground Team” and “Cyclops”
The ransomware landscape has also seen the arrival of new players, “Underground Team“, and “Cyclops“. While the first falls into a category of classic ransomware, with a little twist of proposing their victims a cyber security audit, Cyclops poses a completely new threat. The new ransomware-as-a-service (RaaS) provider proposes a mix between a stealer malware and a ransomware.
The Cyclops group created ransomware capable of infecting all three major platforms: Windows, Linux, and macOS. In an unprecedented move, it has also shared a separate binary specifically geared to steal sensitive data, such as an infected computer name and a number of processes. The latter targets specific files in both Windows and Linux.
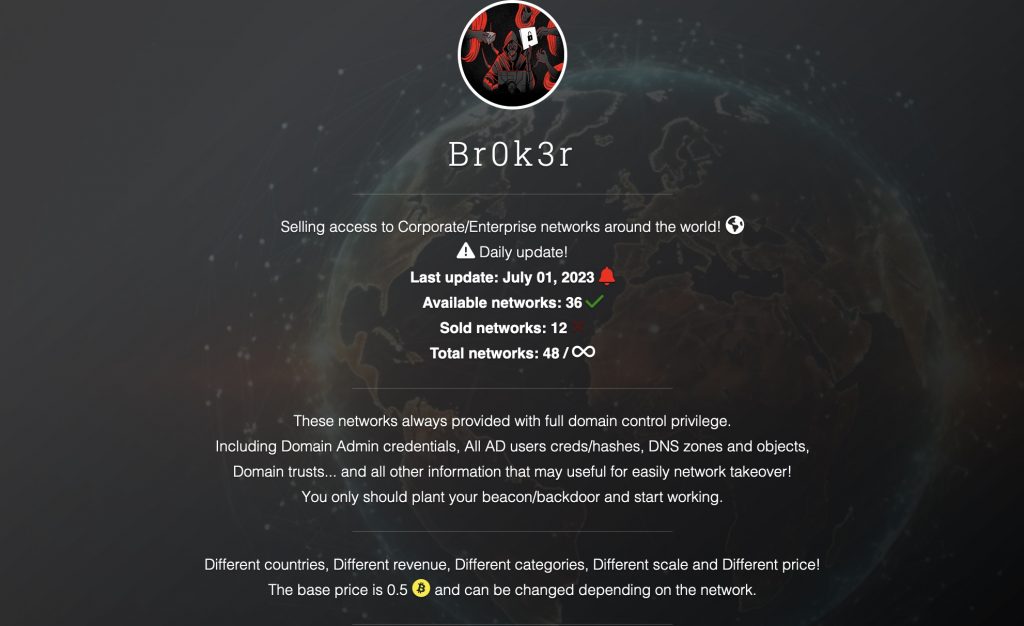
2. Br0k3r: The New Initial Access Broker in the Dark Web
A new initial access broker, known as Br0k3r, has emerged in the dark web. Initial access brokers are cybercriminals who specialize in breaching the security of organizations and selling that access to other criminals. Br0k3r’s claims to have already sold 12 network accesses and is regularly updates its victims list. In the past various ransomware operators, such as LockBit 3.0 claimed they buy access from brokers to speed up the ransomware attack process.
3. Suspected Leader of OPERA1OR Arrested
In a significant victory for law enforcement, the suspected leader of the cybercriminal group OPERA1OR has been arrested. The group has targeted mobile banking services and financial institutions in malware, phishing, and Business Email Compromise (BEC) campaigns. The gang, also known as NX$M$, DESKTOP Group, and Common Raven, is suspected of having stolen between $11 million and $30 million over the last four years in more than 30 attacks spanning 15 countries across Africa, Asia, and Latin America. This arrest sends a strong message to other cybercriminals that their activities are being monitored and that they will be held accountable for their actions.
4. Newly Discovered Chinese Threat Actor Targets European Govt in SmugX campaign
A newly discovered Chinese threat actor has been targeting embassies and foreign affairs ministries in the UK, France, Sweden, Ukraine and the Czech Republic in SmugX phishing attacks. Check Point researchers have been tracking the activity of the threat actor for months. According to the report provided by the company, the attackers utilise HTML Smuggling to target governmental entities in Eastern Europe. This specific campaign has been active since at least December 2022, and is likely a direct continuation of a previously reported campaign attributed to RedDelta.
5. Akira Free Decryptor Shared by Avast
In a positive development, Avast, a cybersecurity software company, has shared a free decryptor for the Akira ransomware. This tool will help victims of Akira recover their encrypted files without paying a ransom, dealing a blow to the cybercriminals behind this threat.
6. Anonymous Sudan Claims to Have Stolen Information Containing 30M Microsoft Accounts, Microsoft Denies Data Breach
Anonymous Sudan has claimed to have stolen information containing 30 million Microsoft accounts. However, Microsoft has denied any data breach, stating that their systems remain secure. Anonymous Sudan is known for debilitating distributed denial-of-service (DDoS) attacks against Western entities in recent months. The group has confirmed their affiliation with pro-Russian hacktivists like Killnet.
7. Another Pro-Russia Crowdsourced DDoS Project, ‘DDoSia,’ Sees Massive Growth
Finally, the pro-Russia crowdsourced DDoS (distributed denial of service) project, ‘DDoSia,’ has seen a massive 2,400% growth in less than a year, with over ten thousand people helping conduct attacks on Western organizations. This alarming growth rate highlights the increasing threat of DDoS attacks and the need for organizations to implement robust DDoS protection measures.
Here it is, the first week of July has been a stark reminder of the dynamic and evolving nature of cyber threats. As new threat actors emerge and existing ones grow in strength, the importance of maintaining robust cybersecurity measures cannot be overstated.
If you liked this article, we advise you to read our previous article about DDoSia “NoName” group attacks. Follow us on Twitter and LinkedIn for more content.
Stay up to date with exposed information online. Kaduu with its cyber threat intelligence service offers an affordable insight into the darknet, social media and deep web.